Overview
- Physical and operational security of our data centers follows AWS/GCP standards
- Network communications use TLS encryption with IDS/IPS, firewalls, and traffic distribution to mitigate DoS attacks
- Virtualization is used to isolate data between users
- Service access is protected with ID/password authentication
- Logs are retained for at least six months
- Vulnerability assessments are performed at least once per year
- The SOC 2 Type 1 audit has been completed
System Architecture
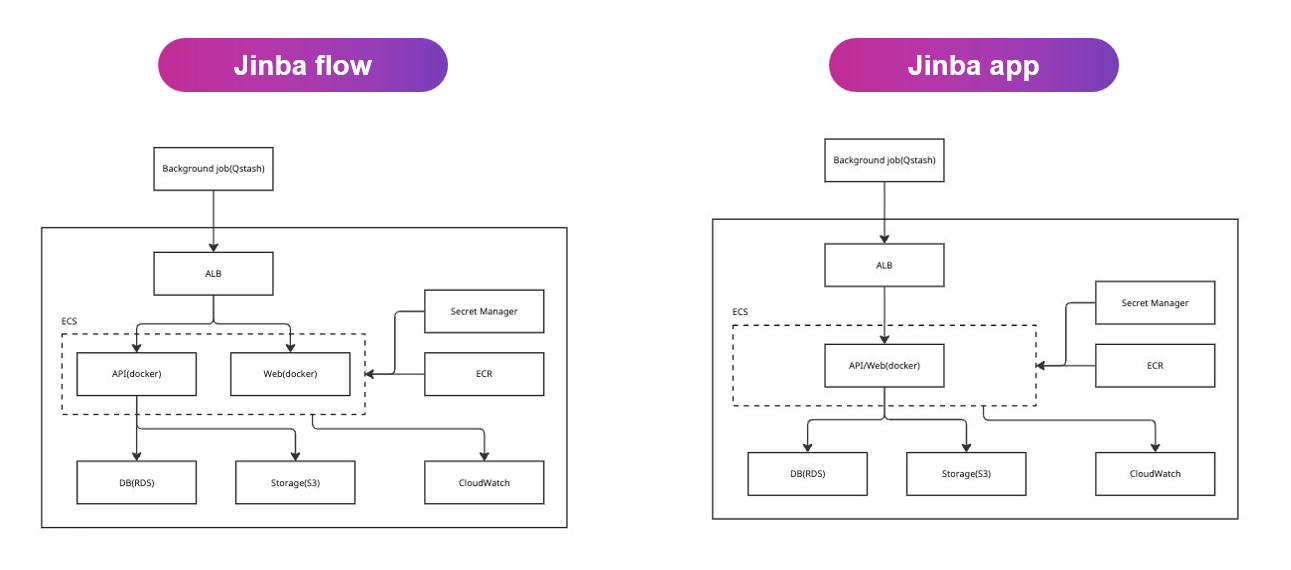
Note: This diagram shows the AWS configuration. Updated August 2025.
 Jinba Flow
Jinba Flow Jinba App
Jinba App